Good question.
A toolbar is considered a browser extension. It is designed to make your Internet browsing experience better. Browsers are the program that gets your web page for you. The most popular browsers are Internet Explorer, Firefox, Chrome and Safari. Each one of these browsers come with their own toolbar. They all have an address bar (for the web page address), buttons to go back or forward pages and bookmarking ability.
So a tool bar is an extension on your browser. Ah...extensions. Extensions do make your browsing experience better. An extension does things that the browser normally does not. An example is streaming that YouTube video from Facebook. Streaming is not something that browsers ordinarily are programmed for. Browsers read the code in web pages and present it to you.
(Want to see what I mean? Simply right click on a blank part of this page and select View Page Source. That is what your web page looks like to the browser. The browser reads that and makes it look like this! :) )
Back to what your browser can do. Remember when every time you went to open a PDF file that you had to have Adobe Reader installed? What happened it that you clicked on the PDF file or link and your browser realized that it couldn't open it and looked on your computer for Adobe Reader and called it to open the file for you. Now, some browsers just open those PDF files in a new tab. Why? Because the browser added that functionality to their programming, or rather, they extended the programming to include PDF files.
Extensions are a good thing when they work to make things better and more interactive. Another extension is Flashplayer that produces graphics on your web site. If you don't have that extension installed, you do not get the graphics.
Most extensions are there, behind the scenes, ready to act when needed.
What makes a toolbar different? First, it takes up space on your browser window. That means that you get to see less of the web page you are viewing. I have seen computers with 9-10 toolbars and the web page got about three inches of space on the computer screen! Not a fun way to view your webpages.
 |
| Your computer screen with toolbars. |
2. Seven other toolbars. Note that they all have a search box.
3. The web page to view.
4. Another toolbar
So if toolbars are so readily available, and they are extensions, then they must be doing something for us, right?
Yes, they do something for us. The problem with toolbars, is, for the most part, they do what we can already do. Most toolbars offer search abilities. Remember that list of browser I mentioned? They all allow you to search for pages in the address bar. Do you another place to search? I would say no.
Some toolbars do add functionality for a very few people. There are toolbars that are specific to a person's field of interest. These toolbars have commands on them that these individuals use regularly. One is the Microsoft Developer Toolbar. It allows the use to view and modify HTML elements on the fly and inspect CSS properties. Very helpful for developers. The QuickStores Toolbar searches shopping sites for you. The CasinoMan Toolbar helps you gamble while browsing. I believe there is a toolbar to watch stocks as well.
The majority of toolbars just help you search and get to your email, or a weather station, or a game. All of which can be bookmarked using the bookmark capability included in your browser.
Not only do these toolbars do what we can already do, and take up space, there was a time period where some toolbars also included malware like Trojans to steal information or corrupt your computer. This is not as common as it once was. (Malware producers have a tendency to move on once they are spotted.) Toolbars can also add functionality to web sites like producing all those ad popups that show up when your move crosses a certain word or phrase. We all want that, right? Do note that some of those pop ups are in the page and the toolbars take them and run with them.
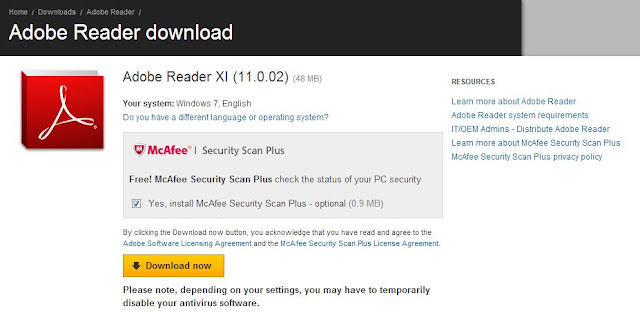
My recommendation. If it is not something that would ruin your day to not have, then get rid of it, Do not download them. (Mind you, they sometimes come with the downloads that you do want. Read about that here.)
Enjoy your time on the Internet!
.....and keep the BugOff !
You can also find me on Facebook, ask to be my friend, I will not turn anyone away.
Follow on Twitter, @BugOffComp
Places that helped me write this article: Free Browser Toolbars; 14 Popular Browser Toolbars; Text Popups; Wikipedia.